Group Partners
Homepage / Networking / Security Protocols

Security Protocols
Virtual Private Networks
Anyone designing a product that will be connected to the internet should be concerned about network security. Green Hills Networking products are pre-integrated with a wide range of security protocols. The broad range of choices makes it easy for the developer to determine the appropriate level of security necessary for their device and deploy it with virtually no impact to their schedules or time to market.
Green Hills Software offers a wide range of security products that are implementations of IETF standardized security protocols. They offer security services such as encryption, authentication, integrity check and replay protection. What protocol to use is determined by the type of application you want to protect.
VPN software enables a user to create a private connection over public networks. By using IPsec, the connection will also be secure, enabling transmission of confidential data over the Internet.
- » IPsec - Internet Protocol Security
- » IKE - Internet Key Exchange
- » SSH - Secure Shell
- » SSL - Secure Socket Layer
- » HTTPS - Secure Embedded Web Server
- » RADIUS - Remote Authentication Dial In User Service
IPsec - Internet Protocol Security
IPsec solves an important problem which arises when embedded systems are connected to the Internet. Since the Internet protocol has no data security built-in, both application and user data is sent in clear text. This enables a third party to inspect or even modify data from the embedded system as it traverses the Internet. For example, passwords are sent in the open and can be seen and used to compromise a system.
Adding IPsec to an embedded system addresses these threats by using strong encryption, integrity, authentication and replay protection. IPsec has become the de facto standard for creating secure networks, and is supported by all major network vendors.
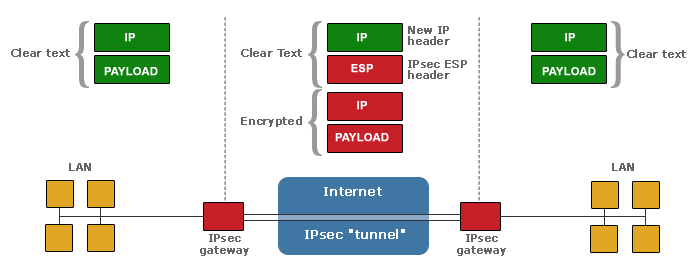
IPsec is designed for both IPv4 and IPv6 operation, and is optimized for deployment in embedded systems.
IKE - Internet Key Exchange
IKE handles exchange of encryption keys when two hosts want to communicate securely using the IPSec protocol. Distributing encryption keys is a difficult task, which requires careful consideration. Before the keys are exchanged, none of the hosts can encrypt any information and if keys are sent in clear text, they can be picked up by someone listening in on the communication. In order to exchange the keys securely, IKE uses state-of-the-art key exchange algorithms, specifically designed to meet the challenge of secure key distribution in embedded systems.
Embedded IKE is an application which generates keys and distributes them securely. IKE stores the keys in a Security Association Database (SADB). IPSec then fetches the necessary keys from SADB when it needs to apply security to an IP packet. A security association contains the encryption keys to use, a specification of the IPSec protocols to apply, the lifetime of the SA, etc.
SSH - Secure Shell
SSH is short for Secure Shell. As the name implies, the protocol creates a secure terminal connection between an SSH client and an SSH server. This means that embedded systems can communicate at the application level over a connection that is encrypted and provides data integrity and replay protection. This effectively eliminates eavesdropping, connection hijacking, IP spoofing and other network-level attacks.
SSL - Secure Socket Layer
SSL was invented by Netscape to include security in their products in order to make communication safe. SSL was originally intended for use with the HTTP protocol used by web servers and browsers but has since evolved to be an important component in all kinds of secure Internet communication.
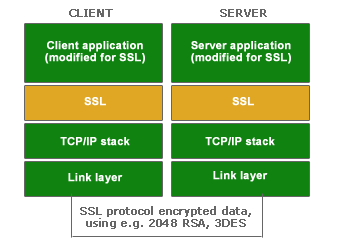
SSL can be used to implement strong authentication, privacy, non-repudiation and integrity for customer specific client or server applications as well as interface to standard Internet applications.
Using SSL to secure your applications in your projects has the advantage that it is already included in all browsers which guarantees portability and ease-of-use for your customers since they can simply start their favorite browser in order to securely manage the system.
HTTPS - Secure Embedded Web Server
Integrating an Embedded Web Server in a dedicated device presents special requirements on the server in terms of memory consumption, performance, security and functional requirements. The Secure Embedded Web Server is a versatile, configurable, high performance HTTP server that has low ROM and RAM footprint. It is specifically designed for operating in an embedded environment.
Since the HTTP protocol does not contain any security features, the HTTPS protocol was invented. It introduces Secure Socket Layer (SSL) functionality in the communication between the Web Server and the browser. This eliminates the risk of most security breaches, and has now become the de facto standard for secure web communication.
The Secure Embedded Web Server has built-in support for SSL which is configurable, and can be removed to get minimum footprint. Secure Embedded Web Server features:
Secure Web Server features:
- » Supports HTTP/1.0 (RFC1945) and HTTP/1.1 (RFC2616)
- » Supports HTTP methods GET, HEAD and POST
- » Supports incoming entities
- » Implements persistent connections (HTTP/1.1)
- » Supports pipelined requests (HTTP/1.1)
- » Supports chunked mode transfer encoding
- » Supports SSL v2, SSL v3 and TLS 1.0 (RFC2246)*
- » Sends target system files upon client requests
- » Supports precompiled HTML files (HTML compiler included)
- » Supports custom function hooks in a CGI-like fashion
- » Implements public API for sending HTML responses
RADIUS - Remote Authentication Dial In User Service
Embedded RADIUS is used to grant remote access dial in users access to an embedded system. Verification is done with either the PAP or the CHAP password schemes.
The Embedded RADIUS client is easy to use and to provides high performance when many logins are in progress. RADIUS is designed for embedded systems and is configurable and under complete control of the user application.
Feature and RFC Conformance for RADIUS:
RADIUS Authentication
- » Supports RFC 2138 and RFC 2548
- » Authentication with PAP, CHAP, MS-CHAP, or MS-CHAPv2
- » Multiple Servers Handled
Delivered in ANSI compliant ”C” source code
Address : Ugur Mumcu St. 43/5 06700 GOP Cankaya, Ankara / TURKEY
Telephone : +90 (312) 447-3016
Fax : +90 (312 ) 447 30 26
E-mail : info@bildesproje.com
Telephone : +90 (312) 447-3016
Fax : +90 (312 ) 447 30 26
E-mail : info@bildesproje.com

