Group Partners
Homepage / Networking / Wireless

- An industry-leading collaboration
- Multiple benefits
- WPA and WPA2
- High Assurance Embedded Cryptographic Toolkit
Network connectivity for a wide range of embedded devices has become extremely common. The latest trend for these connected devices is to drop the leash and get online without wires. While going wireless offers many benefits, it also presents many challenges for developers—such as increased software complexity and added security risks.
An industry-leading collaboration
The Green Hills Platform for Wireless Devices provides developers with a complete Wi-Fi reference development platform for building electronic devices that require secure wireless connectivity. By providing key software technologies in a fully integrated and tested package, the Platform for Wireless Devices accelerates the development of Wi-Fi enabled products. The platform is a result of the collaboration and joint development of industry leaders in security and wireless technology.
Built on the secure foundation of the INTEGRITY® Real-time Operating System (RTOS), the platform incorporates wireless drivers from Qualcomm Atheros with the Silex supplicant agent. These software technologies are integrated and validated on a hardware reference platform consisting of the Logic PD Zoom™ AM3517 eXperimenter Kit with Atheros AR6002/3-based radio modules from Silex Technology.

Multiple benefits
With INTEGRITY, you can isolate the TCP/IP stack and security software in a protected virtual address space and control the acccess, flow of information, and availability of system resources to applications running in other protected parts of the system.
Fast time-to-market
With all of the required software pre-integrated and working together, you don't need to spend valuable time integrating components. Instead, you can focus on adding the unique features and capabilities that will differentiate your product in the market.
Security and reliability
Both security and reliability are critical when connecting devices over a wireless network. With the Green Hills Platform for Wireless Devices your device can take advantage of the proven security and reliability inherent to the INTEGRITY RTOS. INTEGRITY has an unmatched pedigree for security and reliability that includes multiple certifications at the highest levels for security and safety.
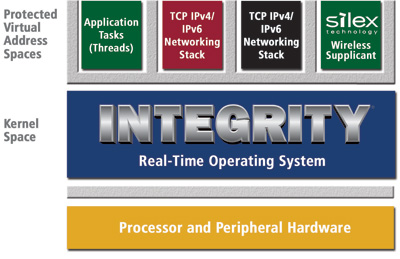
INTEGRITY's separation kernel architecture provides isolation, protection, and controlled access to system resources like network services, devices and even system memory and CPU cycles. Without these protection mechanisms devices are susceptible to infiltration, loss of critical data, and denial of service attacks. The ability to partition resources such as the drivers, network stacks, and applications makes INTEGRITY the clear choice for building secure and reliable systems.
For protecting data in transit, Green Hills has partnered with Silex to bring wireless security together with INTEGRITY. The Silex supplicant agent satisfies the supplicant requirements of both WPA and WPA2 standards. It supports both Personal and Enterprise modes and all the EAP methods mandated by the Wi-Fi Alliance for WPA2 compliance.
WPA and WPA2
In 2003, the Wi-Fi Alliance introduced WPA to rectify the shortcomings of the original Wi-Fi security mechanism, WEP (Wireless Encryption Protocol). WPA2, introduced in 2004, implements all mandatory elements of IEEE's security standard, 802.11i. WPA2 is backwards compatible with WPA, which includes a smaller subset of the 802.11i requirements. WPA and WPA2 can be enabled in two modes – Enterprise and Personal. Both modes provide user authentication and encryption of data traffic (see table at right).
For user authentication, WPA and WPA2 use Pre-Shared Keys (PSK) in Personal Mode and 802.1x/Extensible Authentication Protocol (EAP) in Enterprise Mode. For encryption, WPA uses the Temporal Key Integrity Protocol (TKIP) whereas WPA2 uses the stronger Advanced Encryption Standard (AES). AES satisfies the Federal Information Processing Standard (FIPS) 140-2 specification, a security requirement of many government agencies.
High Assurance Embedded Cryptographic Toolkit (HA-ECT)
Green Hills Software's optional High Assurance Embedded Cryptographic Toolkit (HA-ECT) provides a complete set of cryptographic algorithms for developers requiring a FIPS 140-2 level 1 validation and NSA Suite B-enabled cryptographic module for the Green Hills Platform for Wireless Devices. The HA-ECT standardized cryptographic functionality includes: hash functions; random number generators; secret-key and public-key cryptography including Elliptic Curve Cryptography (ECC) --- enabling developers to quickly build client and/or server-side applications, thus providing end-to-end security.
- Meets government security requirements: The HA-ECT has been ported on a variety of processor platforms, including Power Architecture, ARM, Intel Architecture, and MIPS. HA-ECT enables the developer to create implementations meeting the NSA Suite B Standard- a set of cryptographic specifications that require AES for encryption and elliptic curve cryptography (ECC) for key agreement and digital signatures to secure classified and unclassified communications.
- Reduces time to market : Time to market is the greatest factor in determining your rate of return on investment. All Security Toolkits are designed to be scalable, extensible and portable to reduce your time to market. Having a single FIPS validated crypto toolkit across all your products will increase the security of your product, while maximizing code reuse to reduce your development cycles.
- Flexible and modular code structure: The HA-ECT is highly modular and easily ported to any embedded platform. The toolkit streamlines dynamic memory requiring very little code space and stack usage. Memory requirements for a specific cryptosystem can be determined at run time- prior to any cryptographic function execution. The toolkit can also be built with a set of acceleration techniques providing different levels of speedup, as needed.
- Comprehensive security solution: The HA-ECT provides highly optimized implementations of the NIST elliptic curves as well as NIST prime curves (256, 384, 521), allowing applications to select cryptosystems and extend key lengths at run time. Furthermore, it provides a safe execution environment, and removes the key or other sensitive information from the memory after the cryptographic computations.
- HA-ECT Features: Operating in a FIPS-approved, and expanded mode of operation, HA-ECT provides customers with end-to-end security for both client and server-side platforms
Address : Ugur Mumcu St. 43/5 06700 GOP Cankaya, Ankara / TURKEY
Telephone : +90 (312) 447-3016
Fax : +90 (312 ) 447 30 26
E-mail : info@bildesproje.com
Telephone : +90 (312) 447-3016
Fax : +90 (312 ) 447 30 26
E-mail : info@bildesproje.com

